Archive
Webcast Recording: Limiting Audit Exposure and Managing Risk with Metrics-Driven Identity Analytics
Limiting Audit Exposure and Managing Risk with Metrics-Driven Identity Analytics
Watch the webcast recording here!
There is a new awareness of the strategic value and role of information security in the enterprise. One of the key challenges facing CISO’s today is the pressure to demonstrate continuous compliance – across all business organizations for thousands of users with access to hundreds of applications. Metrics driven Identity Analytics, powered by rich risk analytics, is crucial in measuring how well IT supports the business and manages risk.
Hear from an end user the key elements required to satisfy business and audit requirements for user access certifications and identity controls. Learn how Oracle is leveraging its expertise in identity management, data mining, business processing and business intelligence to give enterprises the tools they need to mitigate risk, build transparency, satisfy compliance mandates and support business decisions.
This webcast covers:
- Key elements for building a strong identity & access governance program
- The advancements in identity and risk analytics offered with Oracle Identity Analytics 11g
- An end-user’s perspective on user access certification use cases and implementation best practices
Watch today to hear about industry best practices from Stuart Lincoln, BNP Paribas, and Neil Gandhi, Principal Product Manager, as they talk about the latest advancements in identity analytics and learn how you too can benefit from making sense of technical identity data and transforming it into business-friendly information that is both insightful and actionable.
Webcast: Limiting Audit Exposure and Managing Risk with Metrics-Driven Identity Analytics
 |
||||||
|
||||||
Do You Need To Reduce Your Audit Exposure?
Today, managers are overwhelmed by the sheer volume of certification reviews and are just certifying users without the appropriate level of attention or analytics. Without proper visibility into user access, managers are unable to perform accurate certification reviews and the result can have negative financial and security consequences. In addition, this results in organizations not being able to sustain a periodic attestation cycle to review user access rights across a wide range of business applications and platforms, thus failing audits. And yes folks, the “Audit Eye” is real! Check it out:
REGISTER NOW
Find out how Oracle can help you keep up with audit requirements.
Webcast, April 12: Automating User Provisioning, A User’s Perspective
| Premieres: | Apr 12, 2011, 14:00 EDT (18:00 GMT) |
User provisioning solutions offer tangible, often quantifiable, benefits. A Forrester Study* based on data from 4 customers concluded an ROI of over 200% and net cost savings of over $8M over 3 years post implementation of Oracle Identity Manager, Oracle’s user provisioning solution. Additional benefits seen were around improved security and a tremendous boost in user productivity.
Join this FREE webcast to find out how Educational Testing Service (ETS), a private nonprofit organization devoted to educational measurement and research, is leveraging Oracle Identity Manager to meet its user administration needs. Hear first-hand from your peer how you can improve security and user productivity in your organization while reducing IT administration, helpdesk and other overhead costs at the same time.
Executive Director, IT, and CISO at Educational Testing Service (ETS)
Jim Moran is an Executive Director, IT, and CISO at Educational Testing Service (ETS). His responsibilities include leadership of Enterprise Architecture, Information Risk, and Information Security for the company. Jim has a long history of conceiving and leading large scale programs and projects, and translating technology trends and strategies into tangible business outcomes.
*Webcast registrants will receive a complimentary copy of: Forrester Study: The Total Economic Impact of Oracle Identity Manager, a commissioned study on behalf of Oracle Corporation
Register Today: Free Oracle Security Online Forum Feb. 24
Oracle and Accenture are holding a new joint event focusing on security. The event will feature great line-up of speakers and sessions that will last from 9:00-1:00pm PT on Thursday, Feb. 24. The event will focus on Security topics that face the enterprise today. The event kicks-off with a keynote presentation detailing emerging security trends and where we think security is headed. in the next decade. Please join us for 30 minutes or the entire day.
- Mary Ann Davidson, Oracle’s Chief Security Officer, on industry-leading standards, technologies, and practices that ensure that Oracle products—and your entire system—remain as secure as possible.
- Jeff Margolies, Partner, Accenture’s Security Practice—on key security trends and solutions to prepare for in 2011 and beyond.
- Vipin Samar, Vice President of Oracle Database Security solutions—on new approaches to protecting data and database infrastructure against evolving threats.
- Tom Kyte, Senior Technical Architect and Oracle Database Guru—on how you can safeguard your enterprise application data with Oracle’s Database Security solutions.
- Nishant Kaushik, Chief Identity Strategist—on how organizations can look to Oracle Identity Management solutions to help them reduce fraud and streamline compliance.
Oracle Identity Management Sessions – Oracle OpenWorld 2010!
I am looking forward to my first Oracle OpenWorld experience! We have some great sessions lined up, including my session on Oracle Identity Analytics, featuring a great customer case study by Express Scripts. Feel free to check it out on Wednesday, Sept 22nd from 4:45PM to 5:45PM at Moscone South, Room 309.
We also have another great session on Oracle Identity Manager 11g, which will be headed by our OIM Product Manager Rajesh Pakkath, and Alexander Bolante from Accenture. This will be on Monday, Sept 20th from 11:00AM to 12:00PM at Moscone South, Room 309.
Our Focus on Identity Management track and available sessions are available here. You can also find them from our Facebook page here and you can also follow us on Twitter at #oow #idm. A small cheat sheet of Oracle Identity Management sessions available below.
| Date & Time | Title of Presentation | Location |
| Mon 11am | Oracle Identity Management 11g Overview | Moscone South 309 |
| Tue 2pm | Simplify IDM with Directory Services – | Moscone South 309 |
| Tues 3:30pm | Oracle’s IDM Strategy (for Sun, Oracle Customers Alike) | Moscone South 310 |
| Wed 1pm | Building a Strong Foundation for Your Cloud with IDM | Moscone South 309 |
| Wed 4:45pm | Complete Identity & Access Governance with OIA 11g | Moscone South 309 |
| Tues 5pm | How Cisco Achieved Large-Scale, Highly Available Access Management | Moscone South 310 |
A Primer on Oracle Identity Manager 11g
As you may already know, Oracle Identity Manager, Oracle’s industry leading identity administration and user provisioning solution, provides operational and business efficiency through centralized administration & complete automation of identity and user provisioning events across the enterprise as well as the extranet. With its latest 11g release, Oracle Identity Manager has now been architecturally optimized for internet-grade scalability in cloud, distributed & in-house environments. This release not only provides enhanced usability to enrich user experience but also provides advanced security features for a granular control of this user experience. Oracle Identity Manager’s superior performance for enterprise-grade deployments makes it an ideal choice for customers seeking an identity administration platform that can serve their changing business needs.
Let’s talk about some of the exciting new innovations with the 11g release, which has seen over 750 man months of development time from a dedicated Engineering team and 1300 man months of QA in this release, not to mention a great team of solution architects and product managers (cannot discount them!).
Rich User Interface
 Oracle Identity Manager 11g provides a multi-tab, desktop-application-like, dynamic Web 2.0 user experience using Oracle’s ADF technology. In addition to great usability, it also provides high performance architecture, such as partial page rendering, real-time scrolling, and transparent paging. This UI framework allows high level meta-data driven customization, such as branding changes, label changes, changes in default sorting schemes, etc. It also includes built-in globalization and accessibility support. It provides very advanced browse, keyword based search and advanced search capabilities. It also tailors the user experiences for different user groups. For example, a task-oriented desktop-application-like UI model for administrators and guided wizards for business end-users. This corporate-wide UI framework contributes to customers’ bottom lines by allowing for greater flexibility in UI customization and reducing the UI learning curve for business end-users and administrators.
Oracle Identity Manager 11g provides a multi-tab, desktop-application-like, dynamic Web 2.0 user experience using Oracle’s ADF technology. In addition to great usability, it also provides high performance architecture, such as partial page rendering, real-time scrolling, and transparent paging. This UI framework allows high level meta-data driven customization, such as branding changes, label changes, changes in default sorting schemes, etc. It also includes built-in globalization and accessibility support. It provides very advanced browse, keyword based search and advanced search capabilities. It also tailors the user experiences for different user groups. For example, a task-oriented desktop-application-like UI model for administrators and guided wizards for business end-users. This corporate-wide UI framework contributes to customers’ bottom lines by allowing for greater flexibility in UI customization and reducing the UI learning curve for business end-users and administrators.
Suite Integration
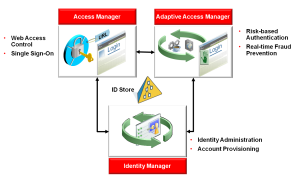 Oracle Identity Manager provides out-of-the-box integration with Oracle Access Manager, Oracle Adaptive Access Manager, and Oracle Identity Navigator Oracle Identity Navigator to significantly reduce the deployment and administrative costs associated with setting up an enterprise deployment topology. Oracle Identity Manager provides the password management (security registration, expired password, forgotten password etc) flows in the login flows initiated by Oracle Access Manager. As an example the end-users clicking on forgotten password link in Oracle Access Manager are seamlessly directed to Oracle Identity Manager. Similarly in an integrated Oracle Identity Manager, Oracle Access Manager and Oracle Adaptive Access Manager environment, the challenge questions for the forgotten password flows may be answered in Oracle Adaptive Access Manager using its virtual devices. Oracle Identity Navigator provides a single, suite-wide SSO-enabled launch-pad to all Identity Management product administrative consoles, which streamlines the user experience and significantly improves the service levels.
Oracle Identity Manager provides out-of-the-box integration with Oracle Access Manager, Oracle Adaptive Access Manager, and Oracle Identity Navigator Oracle Identity Navigator to significantly reduce the deployment and administrative costs associated with setting up an enterprise deployment topology. Oracle Identity Manager provides the password management (security registration, expired password, forgotten password etc) flows in the login flows initiated by Oracle Access Manager. As an example the end-users clicking on forgotten password link in Oracle Access Manager are seamlessly directed to Oracle Identity Manager. Similarly in an integrated Oracle Identity Manager, Oracle Access Manager and Oracle Adaptive Access Manager environment, the challenge questions for the forgotten password flows may be answered in Oracle Adaptive Access Manager using its virtual devices. Oracle Identity Navigator provides a single, suite-wide SSO-enabled launch-pad to all Identity Management product administrative consoles, which streamlines the user experience and significantly improves the service levels.
Request Management
Oracle Identity Manager 11g provides multiple enhancements in the area of request management. It allows users to create requests for business & IT roles, new application accounts, modifications to existing application accounts and application entitlements or privileges. It provides a very flexible, simplified, business-centric, and context sensitive request creation wizard that allows users to create these requests in context of their current views. As an example, the users may create requests for additional roles while viewing their existing role assignments, create request for additional accounts or modification to existing accounts while viewing the provisioned resource lists, or create a complex request including multiple roles & resources for self or others from their home page. By placing the request and approval process closer to the business, enterprises realize better service levels and reduced costs.
Request Templates
Request Management service in Oracle Identity Manager 11g allows administrators to create job or role specific request templates. The template is a simplified overlay on top of a request model that allows the person defining that template to control how a request gets created, and add additional layers of approval, authorization and data restrictions over those already defined in the model. Once configured by the administrators, the request templates provide the much-desired request catalog services to the end users. This results into significantly enhanced usability experience for the end users while creating access requests by providing them with a narrowing down the list of roles, resources and entitlements specific to their job functions.
Approval Workflow Orchestration
 Oracle Identity Manager 11g relies on the Oracle BPEL Process Manager, an integral component of Oracle SOA Suite for its approval workflow and routing engine. Developers can use Oracle JDeveloper as their Integrated Development Environment that offers a rich visual design paradigm for creating and deploying BPEL based processes. Additionally developers can also leverage Oracle BPEL Process Manager’s advanced approval features like email based approvals, serial or parallel approval orchestrations or voting based approval etc. This not only results into significantly faster deployment time, but also provides the architecture agility to adjust workflows quickly when business processes and enterprise policies change for the approval needs.
Oracle Identity Manager 11g relies on the Oracle BPEL Process Manager, an integral component of Oracle SOA Suite for its approval workflow and routing engine. Developers can use Oracle JDeveloper as their Integrated Development Environment that offers a rich visual design paradigm for creating and deploying BPEL based processes. Additionally developers can also leverage Oracle BPEL Process Manager’s advanced approval features like email based approvals, serial or parallel approval orchestrations or voting based approval etc. This not only results into significantly faster deployment time, but also provides the architecture agility to adjust workflows quickly when business processes and enterprise policies change for the approval needs.
Universal Delegated Administration
 Oracle Identity Manager 11g introduces a new feature called Universal Delegated Administration that provides highly flexible authorization model without compromising corporate security policies by moving administration point users like customers, partners, suppliers etc ts as close to the user as possible. Oracle Identity Manager now embeds a fine-grained authorization service based on Oracle Entitlement Server. Using this authorization service, Oracle Identity Manager provides advanced, attribute level delegated administration policies that can be scoped using organization hierarchies and assigned based on roles. For example, administrators can configure a policy stating that users in the helpdesk administrator role can only change the password of the users in certain organizations, or users in the organization administrator role can unlock a locked out user only in their organization. Additionally as enterprises start managing extranet, Universal Delegated Administration enables the enterprises to define complex delegation policies for the extranet identity administration needs for users like customers, partners, suppliers etc.
Oracle Identity Manager 11g introduces a new feature called Universal Delegated Administration that provides highly flexible authorization model without compromising corporate security policies by moving administration point users like customers, partners, suppliers etc ts as close to the user as possible. Oracle Identity Manager now embeds a fine-grained authorization service based on Oracle Entitlement Server. Using this authorization service, Oracle Identity Manager provides advanced, attribute level delegated administration policies that can be scoped using organization hierarchies and assigned based on roles. For example, administrators can configure a policy stating that users in the helpdesk administrator role can only change the password of the users in certain organizations, or users in the organization administrator role can unlock a locked out user only in their organization. Additionally as enterprises start managing extranet, Universal Delegated Administration enables the enterprises to define complex delegation policies for the extranet identity administration needs for users like customers, partners, suppliers etc.
High Performance Reconciliation Engine
Oracle Identity Manager 11g has a new high performance, next generation reconciliation engine that is optimized for handling multi-million user populations. For extranet and enterprise deployments with such high volume scenarios, up to 10x performance gains have been observed when compared with previous releases. Oracle Identity Manager achieves such performance gains by leveraging bulk and batch processing design paradigms directly at the database tier, which altogether avoids increased network latency resulting from middle tier to database tier communication.
Web-based Reconciliation Event Management
 Oracle Identity Manager 11g provides a web based reconciliation event management tool that allows operational administrators to manually (also known as ad-hoc) link high-risk orphan accounts to users. Administrators can also tag these orphan accounts as service accounts, also known as administrator or privileged accounts, which have special life cycle requirements that extend beyond the lifecycle of an assigned user and across the lifecycles of multiple assigned users. Proper management of service accounts can help to eliminate another source of potential orphan accounts.
Oracle Identity Manager 11g provides a web based reconciliation event management tool that allows operational administrators to manually (also known as ad-hoc) link high-risk orphan accounts to users. Administrators can also tag these orphan accounts as service accounts, also known as administrator or privileged accounts, which have special life cycle requirements that extend beyond the lifecycle of an assigned user and across the lifecycles of multiple assigned users. Proper management of service accounts can help to eliminate another source of potential orphan accounts.
Service Oriented Security
Oracle Identity Manager 11g enables in-premise, cloud & partner applications to externalize their identity administration services through its XSD profile SPML web service, which defines the interfaces for applications to interact with Oracle Identity Manager. Additionally, Oracle Identity Manager now supports a LDAP identity repository for managing users, roles and role assignments. The SPML web service can thus be used by applications to achieve LDAP integration. The 11g release also provides new identity services for example, generating a username or a random password for the user, reserving username in LDAP while user registration is going through approval etc. Applications leveraging such a service oriented security strategy are able to benefit from the innovation in Oracle Identity Manager on day 1. Additionally, applications customers looking for enterprise provisioning solutions face a much shorter & smoother learning curve given that they are already well versed with provisioning technology powering their application.
Cost Effective Product Lifecycle Management
Oracle Identity Manager 11g leverages the standard Oracle lifecycle management technologies for installation, configuration, patching and upgrades. Oracle Universal Installer (OUI) is now used to perform a wizard-driven installation and configuration Oracle Identity Manager as well as other Oracle Identity Management 11g products. Pre-configured Oracle WebLogic Server domain templates enable easier deployment to an enterprise topology. Patching and upgrades are handled by Oracle OPatch and Upgrade Assistant technologies respectively. Additionally, Oracle Identity Manager now stores its configuration metadata in Oracle Meta Data Services thereby ensuring that this metadata can be managed independently. Customers will find their total cost of ownership significantly reduced as they do not have to learn and adopt any product specific technologies. Their time to market new features that their business users want is also expected to reduce given the usage of these enterprise-grade lifecycle management technologies.
That sums up the exciting new release highlights of Oracle Identity Manager 11g. For more information, please feel free to visit us on our product website, as well as the 11g Launch Center. Viresh Garg, Director of Product Management for Identity Administration, also provides a great webcast that highlights the OIM 11g release, available here.
Oracle Announces Significant Advances in Application Security With Oracle Identity Management 11g
Check out the article on the Oracle Identity Management 11g launch here.
Introducing Oracle Identity Management 11g – Oracle Webcast
Live Webcast: Introducing Oracle Identity Management 11g
Date: Wednesday, July 21, 2010
Time: 10:00 a.m. PT / 1:00 p.m. ET
Oracle executives introduce a new and revolutionary approach in application security – Oracle Identity Management 11g. Click here to register for the webcast.
Modern enterprise architectures are evolving rapidly, yet many security solutions in use today represent decade old technology. Businesses must adapt swiftly to stay competitive, yet bolted-on security controls impede IT agility. Compliance mandates continue to grow in number, while organizations continue to struggle with their staggering costs and complexity.
Oracle Identity Management 11g redefines the architectures that secure the modern enterprise, ushering in a new era of agile security, rapid ROI, and sustainable compliance. Join us to learn more about the exciting new developments.
Presenter:
 |
Amit Jasuja Vice President Identity Management and Security Products Oracle Corporation |
Benefits of Roles to enable Identity Governance
 Why is it so important for organizations to move towards Role Based Access Control as a means for managing user identities? This mechanism of providing, managing and auditing IT access is starting to be widely accepted, though might not be a the most loved, due to various reasons. Instead of focusing on some of the challenges that may make implementing RBAC somewhat of a pain, I would like to talk about the benefits that organizations gain over time, implementing this model for day to day access governance. Lets start jotting it down:
Why is it so important for organizations to move towards Role Based Access Control as a means for managing user identities? This mechanism of providing, managing and auditing IT access is starting to be widely accepted, though might not be a the most loved, due to various reasons. Instead of focusing on some of the challenges that may make implementing RBAC somewhat of a pain, I would like to talk about the benefits that organizations gain over time, implementing this model for day to day access governance. Lets start jotting it down:
1. Since roles in an organization are relatively persistent with respect to user turnover and task re-assignment, RBAC provides a powerful mechanism for reducing the complexity, cost, and potential for error of assigning users permissions within the organization.
2. Roles support Role Hierarchies, a parent-child relationship, whereby all parent role permissions are inherited by the child role, which is typically more of a specialized role. This prevents role explosion and encourages re-usability in the RBAC model.
3. Roles map naturally to any given line of business and the organizational structure of an enterprise, allowing for a more streamlined and understandable security policy definition and enforcement. This is in contrast to the more conventional and less intuitive process of attempting to administer lower level access control mechanisms directly.
4. RBAC is policy-neutral which enables it to support different security policies. RBAC also directly supports three well-known security principles: least privilege, separation of duties, and data abstraction.
5. RBAC provides superior administrative capabilities with regards to Role content or privilege updates to users. Instead of re-assigning privileges to a large population of users, updating the Role content automatically updates the Role assignment, saving time and resources.
6. RBAC, coupled with provisioning solutions that support RBAC, provides a strong one-two punch for centralized access control in an organization. RBAC truly simplifies the definition, development and maintenance of provisioning processes.
7. Roles bridge the communication gap between business and IT regarding complex access definitions.
8. Roles allow employees to request access more easily and naturally move them towards the concept of least privilege, prohibiting access collectors over time.
9. RBAC allows more efficient reviews of access through Role Vs. Actual assessments, extremely valuable to audit teams in an organization.
These may be just few of the advantages of implementing Role based access control, but they are definitely worth the time and effort of implementing an RBAC solution. Next, I want to talk about the fundamentals of RBAC (without all the technical hoopla!) and then talk about best practices of implementing this model in your organization (with minimal time and effort), so stay tuned.







You must be logged in to post a comment.